Our work on cyber-physical systems is looking at different perspectives of their security and resilience. We have worked extensively on Data Spoofing, in particular in sensor networks but also on LiDAR systems for automotive. We have investigated new means to design threat models that consider the human, physical and cyber aspects of a system. We have also looked at the physical environment as a source of information to bootstrap the security of a system. For example, we have demonstrated that sufficient randomness can be extracted from heart rate IPI to bootstrap security associations between implantable or wearable medical sensors. Finally, we have also designed more efficient ways of performing software attestation.
Hybrid Threats and Protection

In contrast to traditional computer systems cyber-physical systems always have a human, physical and digital aspect to their design. These concepts have traditionally been considered separately in security, with different teams of people and different persons being responsible respectively for the physical security, cyber security or human secturity of a system.
However, attacks do not work in isolation on the physical, digital or human aspects alone but can combine attack steps on each of these elements. For example, it is possible to break the physical security to install the components allowing to compromise the digital aspects of the system. This has been demonstrated by researchers from University of Tulsa on a windmill farm and researchers from Kaspersky on ATMs. These are sometimes referred to as Hybrid Attacks. The relationship between the human, physical and digital aspects of a system is complex: at the same time they each represent an attack vector for the other but they can also help protect each other. We have been working on threat modelling and analysis for such hybrid systems considering at the same time there human, physical and digital aspects. See paper below.
NB. An interesting example of a hybrid attack was mentioned recently in this blog post.
Data Spoofing in Sensor Networks
Malicious data injections pose a severe threat to the systems based on Wireless Sensor Networks (WSNs) since they give the attacker control over the measurements, and on the system’s status and response in turn. Malicious measurements are particularly threatening when used to spoof or mask events of interest, thus eliciting or preventing desirable responses.
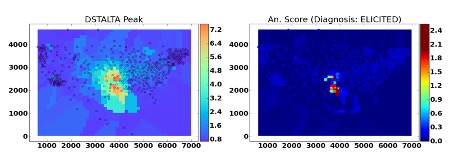
Spoofing and masking attacks are particularly difficult to detect since they depict plausible behaviours, especially if multiple sensors have been compromised and collude to inject a coherent set of malicious measurements. Previous work has tackled the problem through measurements inspection, which analyses the inter-measurements correlations induced by the physical phenomena. However, these techniques consider simplistic attacks and are not robust to collusion. Moreover, they assume highly predictable patterns in the measurements distribution, which are invalidated by the unpredictability of events. We design a set of techniques that effectively detect malicious data injections in the presence of sophisticated collusion strategies, when one or more events manifest. Moreover, we build a methodology to characterise the likely compromised sensors. We also design diagnosis criteria that allow us to distinguish anomalies arising from malicious interference and faults. In contrast with previous work, we test the robustness of our methodology with automated and sophisticated attacks, where the attacker aims to evade detection. Moreover, we estimate quantitatively the WSN degree of resilience and provide a methodology to give a WSN owner an assured degree of resilience by automatically designing the WSN deployment. To deal also with the extreme scenario where the attacker has compromised most of the WSN, we propose a combination with software attestation techniques, which are more reliable when malicious data is originated by a compromised software, but also more expensive, and achieve an excellent trade-off between cost and resilience.
Attacks and Defenses for LiDAR and Perception Systems for Autonomous Vehicles
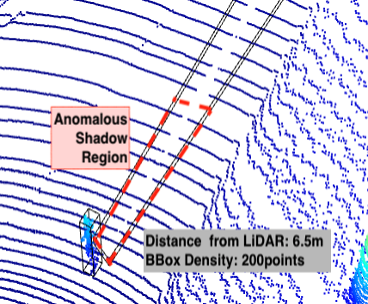
We have developed new algorithms to detect spoofed objects in a 3D point cloud based on the characteristics of the object and of the shadow that the objects would be expected to exhibit. In contrast to some of the related work available in the literature, our work is also applicable to smaller objects such as pedestrians and cyclists. Objects in a scene can be processed in 0.003s-0.021s, which is only a fraction of the time a 3D object detector takes to analyse a scene. By leveraging LiDAR’s default setting of recording a single return signal per direction, we have also shown that it is possible to remove objects from the perception of 3D Object detectors by injecting points behind the target object.
Remote Attestation
Remote software attestation is a technique for verifying the software integrity of devices. However, existing proposals rely on strong assumptions, that hinder their deployment and might even weaken their security. One of such assumptions is that using the maximum known network round-trip time to define the attestation timeout allows all honest devices to reply in time. This assumption does not usually hold in noisy and contested real deployments. We have proposed a novel stochastic approach that significantly improves the overall attestation performance. We have also investigated how this approach can be combined with anomaly detection for sensor data to optimally indentify which sensors may be compromised. A survey of techniques for software attestation has also been compiled.
Generating Randomness from Bio-Physical Signals for securing Body Sensor Networks
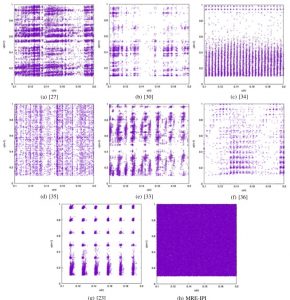
Securely pairing sensors in a given environment is a problem that has been known for some time. For example, medical sensors need to be securely associated with each other when connected to a patient. The fundamental problem is to create a shared key between the sensors (and also manage that key through time). Prior work that we have done in this area has developed protocols for key generation and renewal as well as protocols that pair the sensor together with the help of humans (i.e., by visually confirming which sensors have been paired. However, this requires intervention from clinical staff, who are busy doing other things. It would be helpful to be able to automatically generate shared keys by virtue of the sensors simply being attached to the patient. However, this requires to use the bio-physical signals captured from the patient as a randomness source. We have recently been able to show that it is possible to use heart Inter-Pulse Intervals for this purpose and test this thoroughly using both NIST STS and Dieharder tests. Additionally, this method can be applied to implantable devices as well such as ICDs
Safety and Security in Cyber-Physical Systems
Integrating safety and security methodologies in systems design has always been a challenge. Safety analysis and security analysis are often done through different methods, and by different teams. Yet they both apply to the same system design. Several research questions can be answered at the intersection of safety and security. For example, when do security and safety requirements conflict? or which security attacks can have an impact on the system’s safety properties. We have focussed on the latter question, as determining the attacks that can have an impact on safety becomes increasingly important as the attack surface increases. We have designed a novel way of integrating STAMP/STPA with STRIDE and formal methods to enable us to identify the attacks that, in combination with the cascading effects of the system, lead to the violation of the safety properties. We can then analyse the attack graphs enable an attacker to gain the privileges required for performing those actions and identify the sets of privileges that must be protected and possible countermeasures. The overall methodology is described in this paper. Additionally, we have also developed use-cases showing how variations of this methodology can be applied in the domain of smart-grids, and digital avionics. We are grateful to our colleagues from the Energy Futures Lab at Imperial College and from Airbus, Germany for their collaboration in elaborating these use-cases.