Our research activities are broad and build upon a large amount of work done in Policy Based Network and Systems Management, Distributed Systems, Software Engineering and IoT and Autonomous systems. Some of the work is recent, other aspects date-back a few years but link in various ways with work that we are doing.
Attribution of Cyber Attacks
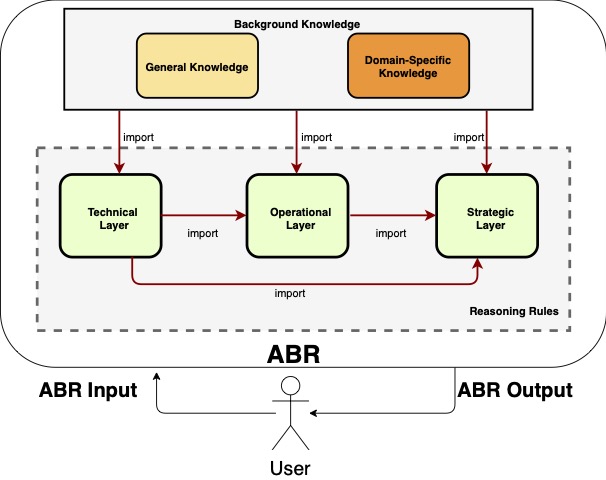
Attribution of cyber attacks is inherently difficult. Firstly, because on a technical evidence level there are many confounding factors. The volume of data to analyse is often large. Code is being traded and reused. Attackers often use deceptive and anti-forensics techniques. As a result there is a need to constantly analyse and reason with conflicting evidence whilst maintaining a rigorous process across a large volume of evidence. Secondly, because attribution can rarely be done on technical factors alone. It is often a process combining technical and social evidence and knowledge must be combined.
To address this challenge we have proposed a new proof of concept tool that can help a forensics analyst during the analysis of forensic evidence and the attribution process. Given the evidence collected from a cyber-attack, our reasoner can assist analysing the evidence even when that evidence is conflicting, by giving hints of the missing evidence or new investigation paths. This tool relies on rules being defined and rules can be used to reason about both the technical and social evidence pertinent to the attack. To cope with incomplete and conflicting evidence the tool uses an automatic reasoner based on argumentation and abductive reasoning. Reasoning rules can be specified regarding background knowledge, processing of the evidence but also about the relative importance of the rules when applied in a given context. This work was developed in the AF-Cyber MSCA Fellowship of Dr Erisa Karafili, now with University of Southampton.
Automated Firewall Rule Analysis and Generation

Firewalls remain the first line of defence for computer networks, and the complexity of firewall configurations makes the task difficult and error prone for human administrators. Automating the analysis and generation of firewall remains a significant challenge. Two main obstacles need to surmounted. First, whilst a number of frameworks allow the analysis and generation of rulesets that avoid e.g. shadowing anomalies, this does not generalise to arbitrary properties and conflicts in the ruleset and does not take into account other aspects such as performance. Second, to generate a firewall configuration it is not sufficient to identify the rules, i.e., the traffic requirements, but the order of the rules in the configuration must be generated as well.
This leads to a non-monotonic specfication in that the addition of one rule may invalidate prior derived rules. Our work on the analysis and generation of firewall rules builds upon our previous experience with conflicts between management and access control policies. First we have shown how it is possible to formalise and analyse policies i.e. rules using Event Calculus. Then we have shown that using a process of formal argumentation and preference reasoning it is possible to generate conflict-free firewall configurations for an arbitrary set of properties and generating the ordering of the rules as well. Finally, we have more recently generalised this to cater for multiple firewalls in the context of a network and inter-firewall anomalies.
Compositional Behaviour and Reliability Models for Adaptive Component-Based Architectures
Although there has been a considerable amount of work on architectural modelling and behavioural analysis of component-based systems, there is a need for approaches that integrate the architectural, behavioural and management aspects of a system. In particular, the lack of support for composability in probabilisitic behavioural models prevents their systematic use for adapting systems based on changes in their non-functional properties. Of these non-functional properties, this work focuses on reliability.
We introduce Probabilistic Component Automata (PCA) for describing the probabilistic behaviour of those systems. Our formalism simultaneously preserves a close correspondence between the behavioural and architectural views of a system in both abstractions and semantics, is composable as behavioural models of composite components are automatically obtained by combining the models of their constituent parts; and lastly is probabilistic thereby enabling analysis of non-functional properties. We show how reliability analysis based on PCA models can be used to perform architectural adaptation on distributed component-based systems and evaluate the computational cost of decentralised adaptation decisions. To mitigate the state-explosion problem, we introduce an algorithm to reduce a component’s PCA model to one that only represents its interface behaviour. We formally show that such model preserves the properties of the original representation whilst the reduced models are more than 80% smaller that the original. A further benefit of the approach is that it allows component profiling and probabilistic interface behaviour to be extracted independently for each component, thereby enabling its exchange between different organisations without revealing commercially sensitive aspects of the components’ implementations.
Detection and Analysis of Ransomware
We present EldeRan, a machine learning approach for dynamically analysing and classifying ransomware. EldeRan monitors a set of actions performed by applications in their first phases of installation checking for characteristics signs of ransomware. Our tests over a dataset of 582 ransomware belonging to 11 families, and with 942 goodware applications, show that El- deRan achieves an area under the ROC curve of 0.995. Fur- thermore, EldeRan works without requiring that an entire ransomware family is available beforehand. These results suggest that dynamic analysis can support ransomware de- tection, since ransomware samples exhibit a set of character- istic features at run-time that are common across families, and that helps the early detection of new variants.
Autonomy and Policy Based Systems
We have worked for many years on policy-based systems where by policies we intend declarative rules that determine how the system should behave under different circumstances. Our work has led to the creation of the Ponder and Ponder2 policy frameworks which were released as open source. As part of this work we have pioneered many techniques for policy enforcement and deployment, as well as formal analysis for policy based systems (including conflict detection), refinement of concrete policies from higher level objectives and automated learning of policy rules from past decisions made by human managers or legacy systems.
Self Managed Cells were introduced as an architectural pattern for building and rapid prototyping of autonomous pervasive systems. In addition, to adaptation through policies, we have developed techniques for programmable peer-to-peer interactions, federation and composition of autonomous systemsas well as techniques for distributed planning with confidentiality.
Data Centric Security
We are broadly interested in techniques for ensuring data quality and protection whether this relates to personal data (privacy), sensor data (healthcare, WSN), crowdsourced data, or large data collections. We have designed techniques for learning privacy policies, defining and enforcing Data Sharing Agreements, protecting derived data (i.e., data obtained by modification or merging of previous data sets), and ensuring data dissemination and usage control including in mobile environments (e.g., in crises management situations). We are also working on techniques for data quality and trustworthinessin crowdsourcing environments.