Wireless Sensor Networks (WSNs) have become popular for monitoring critical infrastructures, military applications, and Internet of Things (IoT) applications.
However, WSNs carry several vulnerabilities in the sensor nodes, the wireless medium, and the environment. In particular, the nodes are vulnerable to tampering on the field, since they are often unattended, physically accessible, and use of tamper-resistant hardware is often too expensive.
Malicious data injections consist of manipulations of the measurements-related data, which threaten the WSN’s mission since they enable an attacker to solicit a wrong system’s response, such as concealing the presence of problems, or raising false alarms.
Measurements inspection is a method for counteracting malicious measurements by exploiting internal correlations in the measurements themselves. Since it does not need extra data it is a lightweight approach, and since it makes no assumption on the attack vector it is caters for several attacks at once.
Our first achievement was to identify the benefits and shortcomings of the current measurements inspection techniques and produce a literature survey, which was published in ACM Computing Surveys: V. P. Illiano and E. C. Lupu. ”Detecting malicious data injections in wireless sensor networks: A survey”, Oct. 2015 . The survey has revealed a large number of algorithms proposed for measurements inspection in sensor measurements. However, malicious data injections are usually tackled together with faulty measurements. Nevertheless, malicious measurements are, by and large, more difficult to detect than faulty measurements, especially when multiple malicious sensors collude and produce measurements that are consistent with each other.
We have designed an initial algorithm, which detects effectively malicious data injections in the presence of sophisticated collusion strategies among a subset of sensor nodes when a single event of interest (e.g. fire, earthquake, power outage) occurs at a time. The detection algorithm selects only information that appears reliable. Colluding sensors are not allowed to compensate for each other in the detection metric whilst still injecting malicious data thanks to an aggregation operator that is accurate in the presence of genuine measurements as well as resistant to malicious data. This work was published in IEEE Transactions on Network and Service Management, V. Illiano and E. Lupu, Detecting malicious data injections in event detection wireless sensor networks, Sept 2015
When multiple events manifest, more complex attack strategies are possible, such as creating false events near legitimate ones, transforming a severe event into several mild events etc. We have then reviewed and re-developed the initial approach to cope with such complex scenarios. Furthermore, we have dealt with the problem of characterisation, i.e. identification of the compromised sensors, and diagnosis, i.e. inferring when the anomaly is most likely malicious or faulty. This work has been published in IEEE Transactions on Dependable and Secure Computing, V. P. Illiano, L. Munoz-Gonzalez, and E. Lupu, Don t fool me!: Detection, characterisation and diagnosis of spoofed and masked events in wireless sensor networks, 2016
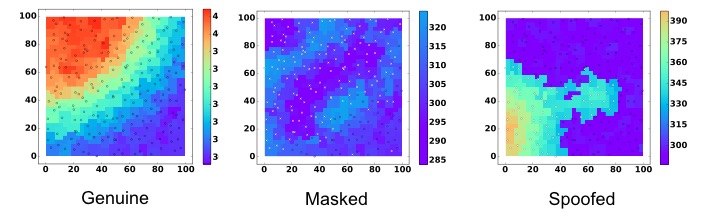
Whilst detection proved highly reliable also in the presence of several colluding nodes, we have witnessed that more genuine nodes are needed to make a correct characterisation of malicious nodes. Hence, we have studied techniques to increase the reliability in identifying malicious nodes through occasional recourse to Software Attestation, a technique that is particularly reliable in detecting compromised software, but is also expensive for the limited computation and energy resources of the sensor nodes. Based on a thorough analysis of the aspects that make measurements inspection and software attestation complementary, we have designed the methods that allow to achieve a reliability as high as for attestation with an overhead as low as for measurements inspection. This work was presented at the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec 2017).